Subscribe
What’s the difference between SAST and DAST?
SAST and DAST are different testing approaches, and each one is used in different phases of the software development life cycle (SDLC) to provide different insights into the health and security of an application.
SAST is a “white box” testing method, meaning the tool has access to the source code of the application it is testing. It examines the code to identify software flaws and weaknesses, as well as critical vulnerabilities like those listed in the OWASP Top 10 list.
Since SAST does not require a running application, it helps developers identify vulnerabilities in the early stages of development, and remediate any identified issues without breaking the build or allowing vulnerabilities to make it into production. SAST gives developers real-time feedback while they code and helps ensure application security is addressed early and often in the SDLC.
DAST is a “black box” testing method, meaning the tool has no access to the application’s source code. It examines an application while it is running to find vulnerabilities in the same way an actual attacker would. By examining an application in its running state, the tool can perform simulated attacks to the system and watch for the system’s response. This provides critical insight into whether the application is vulnerable to outside malicious activities.
See a comprehensive list of the differences between SAST and DAST below.
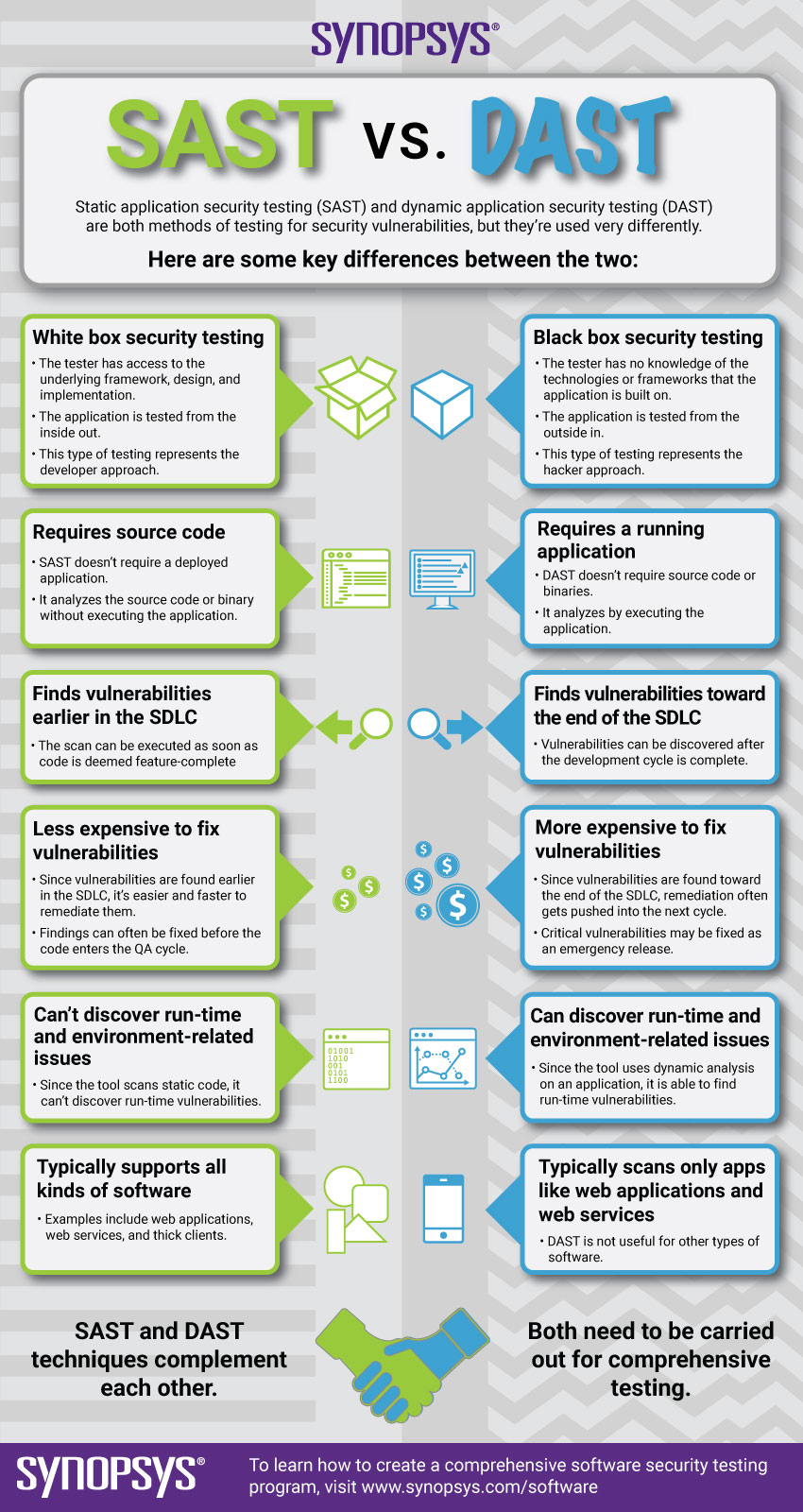
SAST vs. DAST
Static application security testing (SAST) and dynamic application security testing (DAST) are both methods of testing for security vulnerabilities, but they’re used very differently. Here are some key differences between SAST and DAST:
SAST |
DAST |
| White box security testing
The tester has access to the underlying framework, design, and implementation. The application is tested from the inside out. This type of testing represents the developer approach. |
Black box security testing
The tester has no knowledge of the technologies or frameworks that the application is built on. The application is tested from the outside in. This type of testing represents the hacker approach. |
| Requires source code
SAST doesn’t require a deployed application. It analyzes the source code and related dependencies without executing the application. |
Requires a running application
DAST doesn’t require source code or binaries. It analyzes by executing the application. |
Finds vulnerabilities earlier in the SDLC Scans can be run at various stages of the development process, including in the IDE, when codeVulnerabilities can be discovered at the end of the development cycle or in production. |
Finds vulnerabilities toward the end of the SDLC Vulnerabilities can be discovered at the end of the development cycle or in production. |
Less expensive to fix vulnerabilities Since vulnerabilities are found earlier in the SDLC, it’s easier and faster to remediate them. Most issues can be identified and fixed before the code reaches QA. |
Can be more expensive to fix vulnerabilities Since vulnerabilities are found toward the end of the SDLC, remediation often gets pushed into the next cycle. Critical vulnerabilities may be fixed as an emergency release. With solutions like fAST Dynamic, costs can be easily reduced. |
| Can’t discover run-time and environment-related issues
Since SAST tools scan static code, they don’t have visibility into potential runtime vulnerabilities. |
Can discover run-time and environment-related issues
Since the tool uses dynamic analysis, it is able to find runtime vulnerabilities. |
These testing methodologies find different types of vulnerabilities and are most effective when used together in different phases of the software development life cycle. Including both methodologies as part of an organization’s application security strategy provides key insights so you can better understand your overall application security posture.









